Enterprise-Grade Security & Compliance
SynapseMD is built with security and compliance at its core, meeting Australian Privacy Principles, NZ Health Information Privacy Code, and healthcare industry standards.
Certifications & Attestations
ISO 27001
In Progress
SOC 2
In Progress
HIPAA Equivalent
Compliant
Data Residency
Sydney
Primary data center
Melbourne
Backup & redundancy
Auckland
NZ data residency
All patient data is stored in AUS/NZ-based AWS regions, ensuring compliance with local data residency requirements.
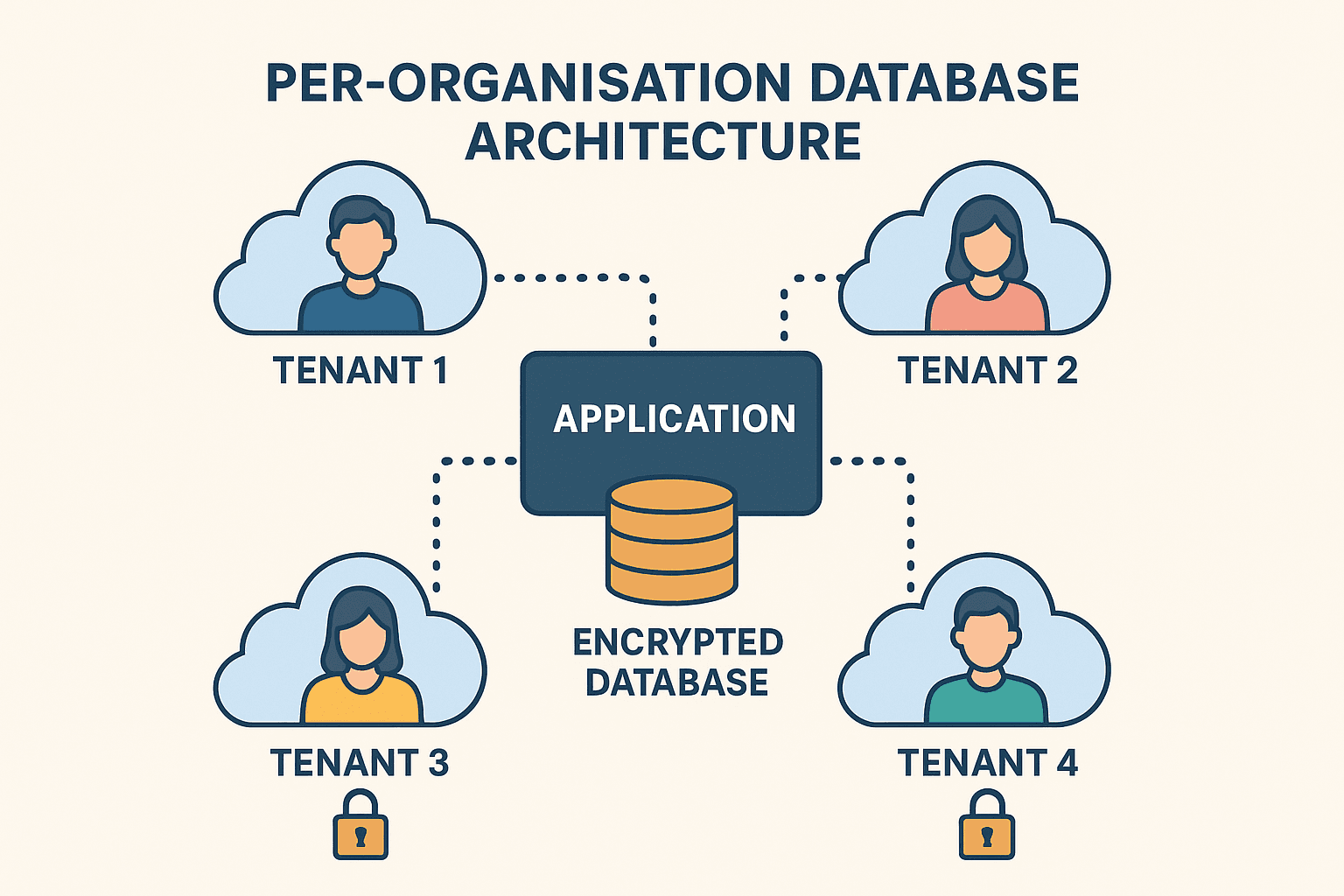
Multi-Tenant Architecture
Database-Per-User Isolation
SynapseMD uses a multi-tenant architecture with database-per-user isolation, where each user gets their own isolated database. Combined with AES-256-GCM column encryption, this ensures:
- Complete data isolation between practices
- No cross-contamination of patient data
- Encrypted database columns with AES-256-GCM
- Enterprise-grade security at every layer
Zero Knowledge Architecture
Your Data, Your Control
SynapseMD implements a zero knowledge architecture for patient and consultation data, meaning we cannot access, read, or decrypt this sensitive information. Only you and authorized members of your practice have the keys to decrypt and access patient and consultation records.
This architecture ensures that even if our systems were compromised, your encrypted patient and consultation data would remain completely inaccessible to unauthorized parties, including SynapseMD staff.
- End-to-end encryption with client-side key management
- SynapseMD cannot decrypt or access your patient and consultation data
- Encryption keys never leave your control
- Complete privacy even from platform administrators
How It Works
Encryption at Source
Patient and consultation data is encrypted on your device before transmission
Key Management
Encryption keys for patient data are managed by your practice, not stored on our servers
Zero Access
We store only encrypted patient and consultation data that we cannot decrypt
Client-Side Decryption
Patient and consultation data is decrypted only on authorized devices within your practice
Maximum Privacy Protection
With zero knowledge architecture, your patient and consultation data is protected even from SynapseMD. This means we cannot access this sensitive information for support purposes, analytics, or any other reason. All patient and consultation data access and decryption happens exclusively within your practice's secure environment.
Privacy & Security Features
Database Encryption
Sensitive database columns are encrypted at rest using AES-256-GCM encryption. Patient data, consultation records, and clinical documents are automatically encrypted before storage, ensuring maximum protection even if database access is compromised.
- AES-256-GCM encryption for all sensitive columns
- Automatic encryption of patient data and documents
- Industry-standard encryption with authentication tags
Scheduled Auto Data Deletion
Automatic deletion of patient and consultation data after a configurable retention period. This ensures compliance with data retention requirements and reduces the risk of unauthorized access to old records.
- Configurable retention periods for patient and consultation data
- Automatic secure deletion after retention period expires
- Compliance with data retention and privacy regulations
Australian Privacy Principles
Full compliance with APPs including data collection, use, disclosure, and security requirements.
NZ Health Information Privacy Code
Adherence to HISO standards and Health Information Privacy Code for New Zealand healthcare providers.
Audit Logs
Complete audit trails for all data access, modifications, and document generation activities.
Incident Response
Comprehensive incident response plan with 24/7 monitoring and rapid response protocols.
Download Security Pack
Get detailed security documentation, compliance attestations, and architecture diagrams for your compliance review.
Questions About Security?
Our compliance team is ready to answer your questions and provide detailed documentation.
Contact Compliance Team